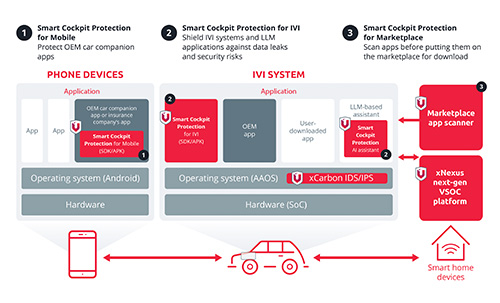
AI-Powered Cockpit Risks: Battling Sensitive Data Leaks
In the first half of 2023 alone, the automotive industry lost over US$9.5 billion to data leaks and personally identifiable information (PII) exposure.* As the landscape of software-defined vehicles (SDVs) evolves, safeguarding user data becomes paramount. Our dynamic approach surpasses outdated static methods, adapting to real-world complexities and an expanding attack surface. VicOne’s Smart Cockpit Protection leads the way with comprehensive protection against malicious AI apps, risky apps, phishing attacks, and privacy breaches — empowering OEMs, suppliers, insurance companies, and marketplace app providers to innovate confidently in the AI cockpit era.
*Source: VicOne Automotive Cyberthreat Landscape Report 2023
Securely Innovate in the AI Cockpit Era With Accurate, Scalable, and Thorough Protection
In-Vehicle AI Guardian
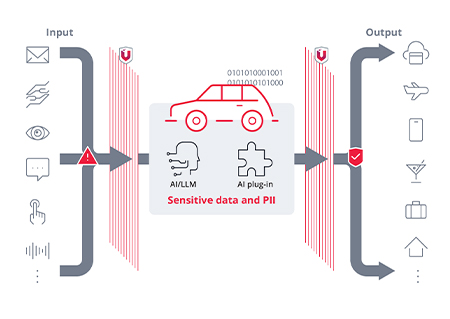
Prevent Sensitive Data Leaks
Our solutions shield your GenAI-based applications from data leaks caused by AI prompt injection, unsecure output, or vulnerable or unsecure third-party plug-ins — covering the OWASP top risks for LLM applications. We support your LLM, whether deployed in the cloud or at the edge.
Browser Defense
Prevent Phishing and Remote Code Execution
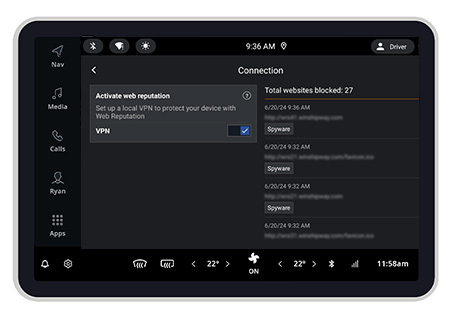
Our solutions can detect vulnerable browsers and malicious URLs, promptly alerting car owners to suspicious website connections. This keeps users from inadvertently sharing sensitive data with phishing sites and effectively prevents remote attacks via browser vulnerabilities that could compromise in-vehicle infotainment (IVI) systems and affect vehicle safety.
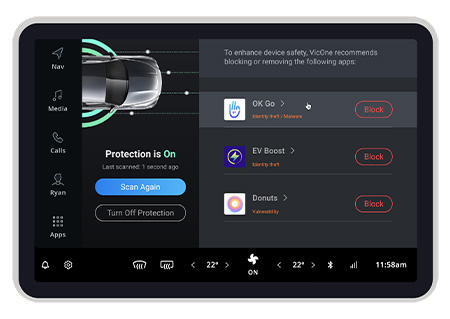
Risky App Detection
Prevent PII Exposure
Our solutions detect risky apps that engage in suspicious API calls, access malicious URLs, or request sensitive or excessive permissions. This ensures robust protection of users’ sensitive data and PII — from IVI systems to car companion mobile apps. Integrated with OEM or IVI supplier systems, our solutions empower car users to block risky apps. Utilizing a proven database with a 100% malicious app protection rate,* we deliver laser-sharp precision in detection.
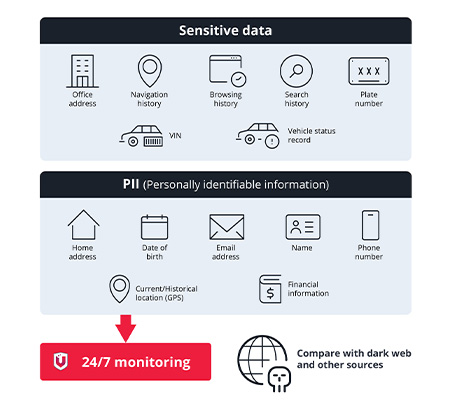
24/7 Data Monitoring
Get Unmatched Coverage
Our solutions vigilantly monitor the dark web and other parts of the internet for leaks of customers’ PII and automotive-related sensitive data, such as VINs. Upon detecting a leakage, we immediately alert customers, empowering them to respond swiftly. Leveraging a proven monitoring service with over 12 billion leaked records found,* we provide the best coverage with earlier warnings in the market.
*Source: Trend Micro ID Security
Safeguarding Every Aspect
of the Smart Cockpit
More Product Features
- Rogue and unsecure Wi-Fi detection: Our solutions detect unsafe Wi-Fi hotspots, identifying potential man-in-the-middle attacks and credential leakage risks. We promptly alert car users with a warning pop-up, ensuring that their security remains uncompromised. Read Recent Case
- One solution for all: We provide versatile deployment and integration options, including SDK and APK, to expedite time to market and streamline implementation.
- Enhanced risk visibility: Integrated with our xNexus next-gen VSOC platform, our solutions extend attack surface visibility from system to application level, empowering OEMs for unified cyber risk management.
- Marketplace app scanner: Our solutions scan for malware, viruses, APK weaknesses, APK vulnerabilities, and malicious AI plug-ins, ensuring that apps are safe before reaching app stores.
- Automotive mobile app protection: By integrating our SDK into automotive mobile apps, such as car companion apps or car insurance apps, OEMs and insurance companies can ensure that their apps run in a secure mobile environment, preventing leakage of personal data.
Our Collaborations
Why VicOne’s Smart Cockpit Protection?
Accelerate Time to Market
We empower OEMs to focus on innovating LLM applications rather than securing them. Our solutions prevent data leaks and defend systems against the OWASP top risks for LLM applications.
Tailored for Automotive Excellence
Our comprehensive solutions address all smart cockpit risks in one package, eliminating separate purchases, testing complexities, and time-to-market delays.
Unmatched
Monitoring
Leveraging our extensive monitoring experience with over 12 billion leaked records found, we provide the best coverage with earlier warnings for data leaks.
Revenue Expansion Opportunities
We enable OEMs to enhance their customer offerings with innovative services built on a secure foundation and to monetize cybersecurity measures to unlock new revenue streams.
Awards We’ve Won
Target Sectors
Consumer OEMs
Commercial OEMs
Tier 1 Suppliers
Car Insurance Companies
Marketplace App Providers
Know More From Our Resources
Gain Insights Into Automotive Cybersecurity
- Read More
 Threat ReportsFebruary 11, 2026From overlapping risk domains in an evolving threat landscape to emerging AI-driven cyberattacks, we examine the critical crossroad facing the auto...
Threat ReportsFebruary 11, 2026From overlapping risk domains in an evolving threat landscape to emerging AI-driven cyberattacks, we examine the critical crossroad facing the auto...